WireGuard VPN
La revisió el 12:11, 28 juny 2024 per Jordi Binefa (discussió | contribucions) (→Exemple de configuració)
WireGuard Server
WireGuard Client
WireGuard Client: Raspberry Pi OS
Exemple de configuració
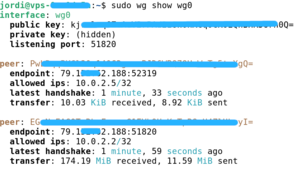
Al servidor:
sudo wg show wg0
Arxiu /etc/wireguard/wg0.conf :
# define the WireGuard service [Interface]
# contents of file wg-private.key that was recently created PrivateKey = SDUV8YmNMk952rabAh8KJwpSHTgOaMam0M8bfoj301Q= # UDP service port; 51820 is a common choice for WireGuard ListenPort = 51820 # define the remote WireGuard interface (client) [Peer] # contents of file wg-public.key on the WireGuard client PublicKey = EG***************************************yI= # the IP address of the client on the WireGuard network AllowedIPs = 10.0.2.2/32 # define the remote WireGuard interface (client) [Peer] # contents of file wg-public.key on the WireGuard client PublicKey = Pw***************************************gQ= # the IP address of the client on the WireGuard network AllowedIPs = 10.0.2.5/32
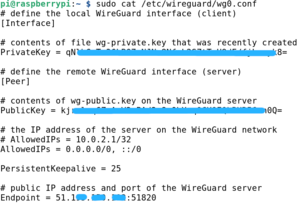
Al client:
sudo cat /etc/wireguard/wg0.conf
Per a que hi hagi visibilitat entre diferents clients de la VPN cal comentar l'exclusivitat de connexió al servidor (10.0.2.1/32) i permetre que altres hi puguin accedir (0.0.0.0/0). I per a mantenir la persistència del túnel s'ha afegit PersistentKeepalive:
# AllowedIPs = 10.0.2.1/32 AllowedIPs = 0.0.0.0/0, ::/0 PersistentKeepalive = 25