Diferència entre revisions de la pàgina «WireGuard VPN»
m (→Exemple de configuració) |
m (→Instal·lació de la VPN WireGuard a Raspberry Pi OS) |
||
| (Hi ha 31 revisions intermèdies del mateix usuari que no es mostren) | |||
| Línia 2: | Línia 2: | ||
[https://wireguard.how/server/debian/ WireGuard Server: Debian] | [https://wireguard.how/server/debian/ WireGuard Server: Debian] | ||
= WireGuard Client = | = WireGuard Client = | ||
| + | [https://wireguard.how/server/debian/ WireGuard Client: Debian] | ||
| + | |||
| + | [https://www.wireguard.com/install/ Instal·ladors del client de WireGuard per altres sistemes operatius] | ||
| + | == Instal·lació de la VPN WireGuard a Raspberry Pi OS == | ||
[https://wireguard.how/client/raspberry-pi-os/ WireGuard Client: Raspberry Pi OS] | [https://wireguard.how/client/raspberry-pi-os/ WireGuard Client: Raspberry Pi OS] | ||
| + | |||
| + | * Des del terminal de la Raspberry Pi: | ||
| + | sudo apt update | ||
| + | sudo apt install '''wireguard''' | ||
| + | |||
| + | * Aneu al servidor WireGuard (no a la Raspberry Pi) i copieu la clau pública: | ||
| + | $ '''sudo wg show wg0''' | ||
| + | interface: wg0 | ||
| + | public key: '''kj***************************************0Q=''' | ||
| + | private key: (hidden) | ||
| + | listening port: 51820 | ||
| + | |||
| + | * Torneu al terminal de la Raspberry Pi: | ||
| + | '''(umask 077 && wg genkey > wg-private.key)''' | ||
| + | '''wg pubkey < wg-private.key > wg-public.key''' | ||
| + | '''cat wg-private.key''' | ||
| + | 4H***************************************E0= | ||
| + | '''cat wg-public.key''' | ||
| + | Tu***************************************TE= | ||
| + | '''sudo nano /etc/wireguard/wg0.conf''' | ||
| + | |||
| + | Aquest ha de ser el contingut de l'arxiu ''/etc/wireguard/wg0.conf'': | ||
| + | # define the local WireGuard interface (client) | ||
| + | [Interface] | ||
| + | |||
| + | # contents of file wg-private.key that was recently created | ||
| + | PrivateKey = '''4H***************************************E0=''' | ||
| + | |||
| + | # define the remote WireGuard interface (server) | ||
| + | [Peer] | ||
| + | |||
| + | # contents of wg-public.key on the WireGuard server | ||
| + | PublicKey = '''kj***************************************0Q=''' | ||
| + | |||
| + | # the IP address of the server on the WireGuard network | ||
| + | # AllowedIPs = 10.0.2.1/32 | ||
| + | AllowedIPs = '''0.0.0.0/0, ::/0''' | ||
| + | |||
| + | '''PersistentKeepalive = 25''' | ||
| + | |||
| + | # public IP address and port of the WireGuard server | ||
| + | Endpoint = '''51.1*.**.**''':51820 | ||
| + | Feu un nou arxiu anomenat ''/etc/network/interfaces.d/wg0'': | ||
| + | sudo nano /etc/network/interfaces.d/wg0 | ||
| + | I poseu aquest contingut (amb la IP de la VPN Wireguard per a aquesta Raspberry Pi): | ||
| + | # indicate that wg0 should be created when the system boots, and on ifup -a | ||
| + | auto wg0 | ||
| + | |||
| + | # describe wg0 as an IPv4 interface with static address | ||
| + | iface wg0 inet static | ||
| + | |||
| + | # the IP address of this client on the WireGuard network | ||
| + | address '''10.0.2.11'''/24 | ||
| + | |||
| + | # before ifup, create the device with this ip link command | ||
| + | pre-up ip link add $IFACE type wireguard | ||
| + | |||
| + | # before ifup, set the WireGuard config from earlier | ||
| + | pre-up wg setconf $IFACE /etc/wireguard/$IFACE.conf | ||
| + | |||
| + | # after ifdown, destroy the wg0 interface | ||
| + | post-down ip link del $IFACE | ||
| + | |||
| + | * Aneu al servidor WireGuard (no a la Raspberry Pi) i editeu l'arxiu ''/etc/wireguard/wg0.conf'' ('''sudo nano /etc/wireguard/wg0.conf''') afegint-hi al final: | ||
| + | # define the remote WireGuard interface (client) | ||
| + | [Peer] | ||
| + | |||
| + | # contents of file wg-public.key on the WireGuard client | ||
| + | PublicKey = '''Tu***************************************TE=''' | ||
| + | |||
| + | # the IP address of the client on the WireGuard network | ||
| + | AllowedIPs = '''10.0.2.11'''/32 | ||
| + | |||
| + | I actualitzeu el servidor de la VPN WireGuard: | ||
| + | '''sudo wg syncconf wg0 /etc/wireguard/wg0.conf''' | ||
| + | * Torneu al terminal de la Raspberry Pi: | ||
| + | '''sudo ifup wg0''' | ||
| + | Verifiqueu que podeu veure la interfície de xarxa ''wg0'': | ||
| + | '''ip address show dev wg0''' | ||
| + | Verifiqueu que hi ha hagut tràfic entre el servidor de la VPN WireGuard i el client (a la Raspberry Pi): | ||
| + | '''sudo wg show wg0''' | ||
| + | |||
| + | = WireGuard a Android = | ||
| + | [https://download.wireguard.com/android-client/ Client d'Android de l'aplicació WireGuard] | ||
| + | |||
| + | * Per a crear les claus privada i pública per a Android des del servidor: | ||
| + | |||
| + | [https://serversideup.net/generating-wireguard-qr-codes-for-fast-mobile-deployments/ Generating WireGuard QR codes for fast mobile deployments] | ||
| + | |||
| + | * Configuració de l'aplicació d'Android: | ||
| + | |||
| + | [https://serversideup.net/how-to-configure-a-wireguard-android-vpn-client/ How to configure a WireGuard Android VPN Client] | ||
| + | |||
| + | L'apartat ''Add your client to your server'' no m'ha funcionat. Per a que em funcioni he fet: | ||
| + | |||
| + | He afegit al final de l'arxiu '''/etc/wireguard/wg0.conf''' del servidor (l'adreça '''10.0.2.6''' és la IP que tindrà el mòbil a la VPN WireGuard): | ||
| + | [Peer] | ||
| + | |||
| + | PublicKey = Fn***************************************RU= | ||
| + | |||
| + | AllowedIPs = '''10.0.2.6'''/32 | ||
| + | I al final li he dit a WireGuard que recarregui la nova configuració: | ||
| + | sudo wg syncconf wg0 /etc/wireguard/wg0.conf | ||
| + | |||
= Exemple de configuració = | = Exemple de configuració = | ||
| − | Al servidor | + | == Al servidor == |
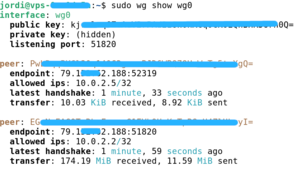
sudo wg show wg0 | sudo wg show wg0 | ||
[[Image:WgServer00.png|center|thumb|Server:~$ sudo wg show wg0]] | [[Image:WgServer00.png|center|thumb|Server:~$ sudo wg show wg0]] | ||
| − | Al client | + | |
| + | Arxiu ''/etc/wireguard/wg0.conf'' : | ||
| + | # define the WireGuard service | ||
| + | '''[Interface]''' | ||
| + | |||
| + | # contents of file wg-private.key that was recently created | ||
| + | PrivateKey = SD***************************************1Q= | ||
| + | |||
| + | # UDP service port; 51820 is a common choice for WireGuard | ||
| + | ListenPort = 51820 | ||
| + | |||
| + | # define the remote WireGuard interface (client) | ||
| + | '''[Peer]''' | ||
| + | |||
| + | # contents of file wg-public.key on the WireGuard client | ||
| + | PublicKey = EG***************************************yI= | ||
| + | |||
| + | # the IP address of the client on the WireGuard network | ||
| + | AllowedIPs = 10.0.2.2/32 | ||
| + | |||
| + | # define the remote WireGuard interface (client) | ||
| + | '''[Peer]''' | ||
| + | |||
| + | # contents of file wg-public.key on the WireGuard client | ||
| + | PublicKey = Pw***************************************gQ= | ||
| + | |||
| + | # the IP address of the client on the WireGuard network | ||
| + | AllowedIPs = 10.0.2.5/32 | ||
| + | |||
| + | |||
| + | == Al client == | ||
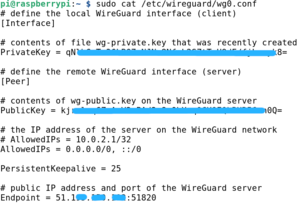
sudo cat /etc/wireguard/wg0.conf | sudo cat /etc/wireguard/wg0.conf | ||
[[Image:WgClient00.png|center|thumb|Client:~$ sudo cat /etc/wireguard/wg0.conf]] | [[Image:WgClient00.png|center|thumb|Client:~$ sudo cat /etc/wireguard/wg0.conf]] | ||
| + | Per a que hi hagi visibilitat entre diferents clients de la VPN cal comentar l'exclusivitat de connexió al servidor (''10.0.2.1/32'') i permetre que altres hi puguin accedir (''0.0.0.0/0''). I per a mantenir la persistència del túnel s'ha afegit ''PersistentKeepalive'': | ||
| + | # AllowedIPs = 10.0.2.1/32 | ||
| + | AllowedIPs = '''0.0.0.0/0, ::/0''' | ||
| + | |||
| + | '''PersistentKeepalive''' = 25 | ||
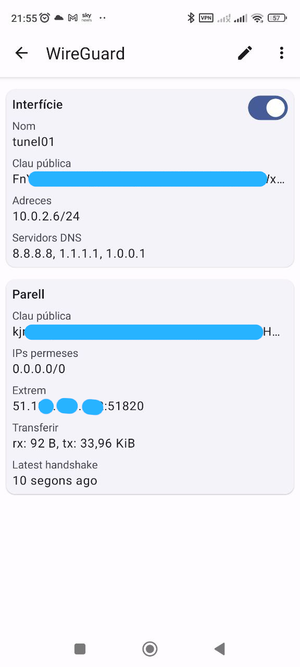
| + | == A un client Android == | ||
| + | '''Interfície''' correspon al mòbil | ||
| + | |||
| + | '''Parell''' (''Peer'') correspon al servidor a on és allotjada la VPN WireGuard | ||
| + | |||
| + | Podeu editar els valors prement la icona del llapis | ||
| + | |||
| + | [[Image:WgAndroid00.png|center|thumb|Client Android]] | ||
Revisió de 18:47, 30 juny 2024
Contingut
WireGuard Server
WireGuard Client
Instal·ladors del client de WireGuard per altres sistemes operatius
Instal·lació de la VPN WireGuard a Raspberry Pi OS
WireGuard Client: Raspberry Pi OS
- Des del terminal de la Raspberry Pi:
sudo apt update sudo apt install wireguard
- Aneu al servidor WireGuard (no a la Raspberry Pi) i copieu la clau pública:
$ sudo wg show wg0 interface: wg0 public key: kj***************************************0Q= private key: (hidden) listening port: 51820
- Torneu al terminal de la Raspberry Pi:
(umask 077 && wg genkey > wg-private.key) wg pubkey < wg-private.key > wg-public.key cat wg-private.key 4H***************************************E0= cat wg-public.key Tu***************************************TE= sudo nano /etc/wireguard/wg0.conf
Aquest ha de ser el contingut de l'arxiu /etc/wireguard/wg0.conf:
# define the local WireGuard interface (client) [Interface] # contents of file wg-private.key that was recently created PrivateKey = 4H***************************************E0= # define the remote WireGuard interface (server) [Peer] # contents of wg-public.key on the WireGuard server PublicKey = kj***************************************0Q= # the IP address of the server on the WireGuard network # AllowedIPs = 10.0.2.1/32 AllowedIPs = 0.0.0.0/0, ::/0 PersistentKeepalive = 25 # public IP address and port of the WireGuard server Endpoint = 51.1*.**.**:51820
Feu un nou arxiu anomenat /etc/network/interfaces.d/wg0:
sudo nano /etc/network/interfaces.d/wg0
I poseu aquest contingut (amb la IP de la VPN Wireguard per a aquesta Raspberry Pi):
# indicate that wg0 should be created when the system boots, and on ifup -a
auto wg0
# describe wg0 as an IPv4 interface with static address
iface wg0 inet static
# the IP address of this client on the WireGuard network
address 10.0.2.11/24
# before ifup, create the device with this ip link command
pre-up ip link add $IFACE type wireguard
# before ifup, set the WireGuard config from earlier
pre-up wg setconf $IFACE /etc/wireguard/$IFACE.conf
# after ifdown, destroy the wg0 interface
post-down ip link del $IFACE
- Aneu al servidor WireGuard (no a la Raspberry Pi) i editeu l'arxiu /etc/wireguard/wg0.conf (sudo nano /etc/wireguard/wg0.conf) afegint-hi al final:
# define the remote WireGuard interface (client) [Peer] # contents of file wg-public.key on the WireGuard client PublicKey = Tu***************************************TE= # the IP address of the client on the WireGuard network AllowedIPs = 10.0.2.11/32
I actualitzeu el servidor de la VPN WireGuard:
sudo wg syncconf wg0 /etc/wireguard/wg0.conf
- Torneu al terminal de la Raspberry Pi:
sudo ifup wg0
Verifiqueu que podeu veure la interfície de xarxa wg0:
ip address show dev wg0
Verifiqueu que hi ha hagut tràfic entre el servidor de la VPN WireGuard i el client (a la Raspberry Pi):
sudo wg show wg0
WireGuard a Android
Client d'Android de l'aplicació WireGuard
- Per a crear les claus privada i pública per a Android des del servidor:
Generating WireGuard QR codes for fast mobile deployments
- Configuració de l'aplicació d'Android:
How to configure a WireGuard Android VPN Client
L'apartat Add your client to your server no m'ha funcionat. Per a que em funcioni he fet:
He afegit al final de l'arxiu /etc/wireguard/wg0.conf del servidor (l'adreça 10.0.2.6 és la IP que tindrà el mòbil a la VPN WireGuard):
[Peer] PublicKey = Fn***************************************RU= AllowedIPs = 10.0.2.6/32
I al final li he dit a WireGuard que recarregui la nova configuració:
sudo wg syncconf wg0 /etc/wireguard/wg0.conf
Exemple de configuració
Al servidor
sudo wg show wg0
Arxiu /etc/wireguard/wg0.conf :
# define the WireGuard service [Interface] # contents of file wg-private.key that was recently created PrivateKey = SD***************************************1Q= # UDP service port; 51820 is a common choice for WireGuard ListenPort = 51820 # define the remote WireGuard interface (client) [Peer] # contents of file wg-public.key on the WireGuard client PublicKey = EG***************************************yI= # the IP address of the client on the WireGuard network AllowedIPs = 10.0.2.2/32 # define the remote WireGuard interface (client) [Peer] # contents of file wg-public.key on the WireGuard client PublicKey = Pw***************************************gQ= # the IP address of the client on the WireGuard network AllowedIPs = 10.0.2.5/32
Al client
sudo cat /etc/wireguard/wg0.conf
Per a que hi hagi visibilitat entre diferents clients de la VPN cal comentar l'exclusivitat de connexió al servidor (10.0.2.1/32) i permetre que altres hi puguin accedir (0.0.0.0/0). I per a mantenir la persistència del túnel s'ha afegit PersistentKeepalive:
# AllowedIPs = 10.0.2.1/32 AllowedIPs = 0.0.0.0/0, ::/0 PersistentKeepalive = 25
A un client Android
Interfície correspon al mòbil
Parell (Peer) correspon al servidor a on és allotjada la VPN WireGuard
Podeu editar els valors prement la icona del llapis